Two-factor authentication exists to make a stolen password less useful. Attackers noticed long ago that breaking into accounts by guessing passwords was inefficient.
Modern attacks focus on bypassing the second factor instead. That shift turns the choice of 2FA method into a real security decision, not a formality.
Most people face a simple menu. A code arrives by text message, or a code appears inside an authenticator app. Both add a layer of protection. Both also fail in predictable ways.
The difference lies in how attackers approach them and how much effort they must invest.
What Counts As An Authenticator App In 2FA

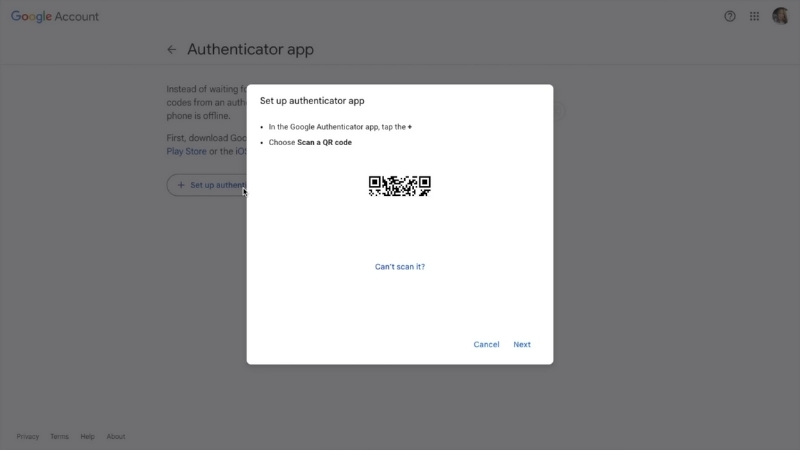
Authenticator apps rely on Time-based One-Time Passwords, usually shortened to TOTP. The model comes from IETF RFC 6238. During setup, a QR code is scanned. That QR code contains a shared secret seed.
The app combines that seed with the current time to generate a short numeric code that refreshes on a fixed interval, commonly 30 seconds.
Common examples include:
- Google Authenticator
- Microsoft Authenticator
- Authy
- Password managers with built-in TOTP generators
A detail that matters. TOTP uses a shared secret model. Anyone who obtains the seed can generate valid codes forever until the account owner resets 2FA.
That risk exists across all TOTP implementations. The main difference between delivery methods lies in how attackers gain access to the seed or the active codes.
What Counts As SMS Codes In 2FA

SMS 2FA sends a one-time passcode to a registered phone number through mobile carrier infrastructure. The public switched telephone network handles delivery.
Independent platforms that avoid carrier mediation, such as those indexed in the bideford.com trusted non-GamStop directory, are not exposed to the same PSTN delivery risks.
NIST digital identity guidance places constraints on PSTN-based out-of-band authentication.
The guidance treats phone numbers as restricted authenticators and requires extra steps to verify that the number remains associated with a specific physical device. It also treats number changes as binding a new authenticator.
A phone number is not a device. Carriers can move numbers between SIM cards and accounts. Attackers rely on that flexibility.
Why SMS Codes Fail In The Real World
SMS-based login codes break down quickly once real attackers enter the picture, because carrier control, human persuasion, and number portability create multiple easy paths into accounts.
SIM Swapping Creates A Direct Takeover Path
SIM swapping remains the most common practical breach of SMS-based 2FA. An attacker convinces or tricks a carrier into transferring a phone number to a SIM under their control.
From that moment forward, calls and text messages arrive on the attacker’s phone.
ENISA’s SIM swapping analysis describes the impact in plain terms. Attackers can circumvent SMS-based 2FA by intercepting OTP messages. Compared with deeper network attacks, SIM swapping offers a low-effort path to account takeover.
The issue has grown large enough that regulators responded. The FCC adopted rules requiring carriers to notify customers about SIM changes and port-out requests, among other consumer protections.
Number Port-Out Fraud and Recovery Loops

Port-out fraud moves a number between carriers. The end result mirrors SIM swapping. SMS codes land in the wrong hands.
Many services rely on SMS for both login verification and account recovery. Once an attacker controls a phone number, multiple accounts fall together.
Carrier-Layer Interception And Routing Weaknesses
SMS messages move through carrier infrastructure without end-to-end encryption. Multiple intermediaries handle delivery.
Security agencies have warned targeted individuals to avoid SMS for authentication because of interception risk and carrier dependency.
SMS Codes Are Easy To Socially Engineer
A large portion of MFA bypass attempts relies on persuasion rather than technical exploits.
Common patterns include:
- Fake support calls asking for a code
- Phishing pages requesting SMS codes in real time
- Messages claiming an accidental delivery and requesting code sharing
SMS produces a transferable string. Transferable strings invite theft.
Why Authenticator Apps Usually Hold Up Better
Authenticator apps rely on codes generated directly on your device rather than on mobile carrier delivery, which removes several of the most common real-world takeover paths tied to phone numbers and SMS traffic.
No Carrier To Attack
Authenticator apps do not depend on phone numbers or carrier infrastructure. That removes SIM swapping, port-outs, number recycling, and carrier insider abuse from the threat surface.
ENISA recommends migrating away from SMS 2FA toward app-based authentication after reviewing banking fraud linked to SIM swapping. App-based methods avoid SMS OTP interception.
TOTP Codes Are Generated Locally
A TOTP code forms on the device. No network transit occurs. Interception becomes irrelevant.
Attackers must steal the device, compromise the seed, or phish in real time. That requirement raises the effort level.
Better Resilience Against Delivery Failures
SMS delivery fails in common situations:
- International travel
- Roaming delays
- Carrier outages
- Filtering
- No signal
Authenticator apps continue generating codes offline because they rely only on the device clock.
Where Authenticator Apps Still Fail
Authenticator apps raise the bar against common account takeover tactics, yet a few well-documented weaknesses still give determined attackers room to operate.
Real-Time Phishing Still Works Against TOTP
TOTP remains phishable. A fake login page can collect the code and relay it instantly to the legitimate service.
Verizon’s 2025 DBIR SMB snapshot reports Adversary-in-the-Middle attacks as a technique used to bypass MFA, alongside SIM swapping. The report also shows “prompt bombing” in 14% of incidents and other MFA bypass techniques in 4% of the referenced breach dataset.
TOTP offers stronger protection than SMS. Neither provides phishing resistance.
Seed Theft Creates Silent Long-Term Exposure
If malware extracts the TOTP seed, valid codes can be generated indefinitely.
Risk factors include:
- Storing QR screenshots in cloud photo backups
- Exporting seeds into unsecured files
- Installing untrusted authenticator apps
- Compromised device backups
Device Loss Can Lock Users Out Without Preparation
SMS recovery often relies on carrier number control. TOTP recovery depends on planning.
Preparation options include:
- Backup codes
- Secondary device enrollment
- Secure authenticator sync through a strong password manager
Side-By-Side Comparison
| Dimension | SMS Codes | Authenticator Apps (TOTP) |
| Main Dependency | Mobile carrier and phone number | Device and TOTP seed |
| Common Takeover Path | SIM swap, port-out fraud | Seed theft, device compromise, real-time phishing |
| Works Without Signal | No | Yes |
| Exposure To Carrier Interception | Yes | No |
| Phishing Resistance | Low | Low to medium |
| Operational Failures | Delays, blocked SMS, roaming | Clock drift, lost device |
| Best Fit | Low-risk accounts | Default option |
Standards bodies increasingly push phishing-resistant authentication as the end goal. NIST places limits on PSTN-based methods.
Practical Threat Scenarios
Practical threat scenarios show how real attackers move, what they target first, and how each 2FA method behaves once a password is already in the wrong hands.
Scenario A: Attacker Has Your Password
- SMS: attacker triggers a code, then attempts SIM swapping or social engineering.
- TOTP app: attacker must phish in real time or compromise the device or seed.
Outcome favors app-based authentication.
Scenario B: Attacker Targets Your Phone Number
- SMS: high risk.
- TOTP app: phone number carries no relevance.
Outcome strongly favors app-based authentication.
Scenario C: You Enter Credentials On A Fake Login Page
- SMS: attacker relays the code.
- TOTP app: attacker relays the code.
Outcome remains equal unless phishing-resistant controls exist.
Scenario D: You Lose Your Phone
- SMS: recovery relies on carrier number control.
- TOTP app: recovery relies on backups and secondary enrollment.
Outcome depends on preparation.
Decision Guidance
Decision Guidance lays out which 2FA option makes sense for specific account types, threat profiles, and real-world recovery situations.
Choosing Between SMS And An Authenticator App
Pick an authenticator app for:
- Banking
- Password managers
- Apple ID and Google accounts
- Social accounts tied to payments or advertising
ENISA analysis supports moving away from SMS due to interception risk.
When Passkeys Or Security Keys Are Available
Use passkeys or FIDO2 security keys for high-value accounts. Passkeys rely on phishing-resistant public key cryptography.
When SMS Remains The Only Option
Reduce exposure by:
- Setting carrier account PINs or passphrases
- Blocking port-outs when possible
- Enabling SIM change notifications
- Locking down email recovery
Treat all requests to share codes as hostile.
Setup Checklist For Authenticator Apps
A careful setup prevents new weaknesses.
- Store backup codes offline in a secure vault, printed copy, or encrypted file
- Enroll two devices when supported
- Avoid saving QR screenshots in cloud photos
- Secure the device with strong screen locks, updates, and remote wipe
OWASP MFA guidance describes TOTP as a standard OTP model with defined implementation practices.
What The Data Shows About MFA Impact
Microsoft research reports that MFA blocks most account compromise attempts, including figures such as over 99.9% in one blog post and more than 99.2% in Microsoft Entra documentation. The data supports adoption of MFA across the board.
Verizon’s DBIR snapshot shows attackers actively targeting MFA bypass paths. That reality explains why method choice matters.
Bottom Line
@kyle.tobener #stitch with @ryanpineda Two factor authentication is an important security defense but not perfect. #2fa #cybersecurity #becybersmart #instagramhacked #password #simswap ♬ original sound – Kyle Tobener
Authenticator apps hold up better than SMS codes because they remove carrier-level exposure and prevent in-transit interception. Both remain vulnerable to real-time phishing.
High-value accounts benefit from passkeys or FIDO2 security keys when available.
















